Implementation of BYOD Security Policy in Malaysia Institutions of Higher Learning (MIHL): An Overview
DOI:
https://doi.org/10.37934/araset.33.2.114Keywords:
Bring Your Own Devices (BYOD), BYOD Security Policy, information security, MalaysiaAbstract
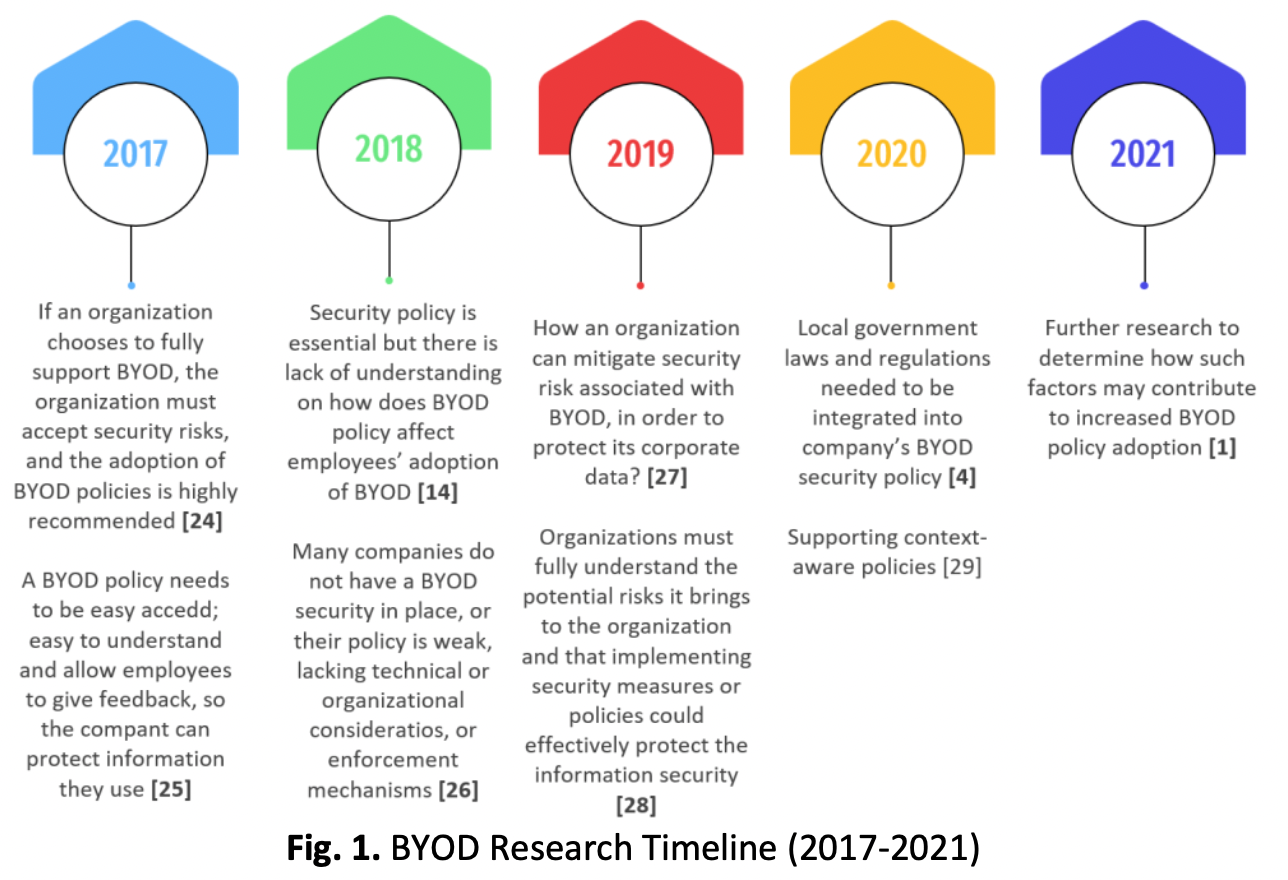
The BYOD Security Policy (BYOD-SP) constitutes formal documentation protecting sensitive data and information during BYOD implementation in an organization. The BYOD environment in an organization might face threats if information assets security is not prioritized before initializing BYOD. Releasing BYOD-SP is one of the key strategies to safeguard safety in BYOD implementation and to ensure users adhere to the BYOD-SP. It can also increase the understanding of ways to protect the BYOD environment from any risk. Hence, this study explores the current situation of BYOD, specifically in Malaysian tertiary education institutions, and the compulsory components that should be highlighted in the BYOD-SP. The implementation of (BYOD-SP) in Malaysian Institutions of Higher Learning (IHL) has led to a sense of discouragement, with only a few institutions being able to clearly outline their implementation strategy, in contrast to what has been done by foreign universities. This has resulted in a lack of information and understanding about the components of BYOD-SP in the Malaysian environment, making it difficult to make deeper comparisons. Understanding the current practice of BYOD can provide a more comprehensive study of a suitable model, cybersecurity framework, or other features to prepare a comprehensive BYOD-SP documentation on campus. As the BYOD implementation is underway, this study could increase awareness of all aspects of BYOD to aid organizations in formulating the BYOD-SP document. This could encourage BYOD players to achieve maximum information security protection.
Downloads