A Proposed Framework of Vulnerability Assessment and Penetration Testing (VAPT) in Cloud Computing Environments from Penetration Tester Perspective
DOI:
https://doi.org/10.37934/araset.39.1.114Keywords:
Cloud computing, penetration testing, SaaS, PaaS, IaaS, VAPT, Pentesting methodologyAbstract
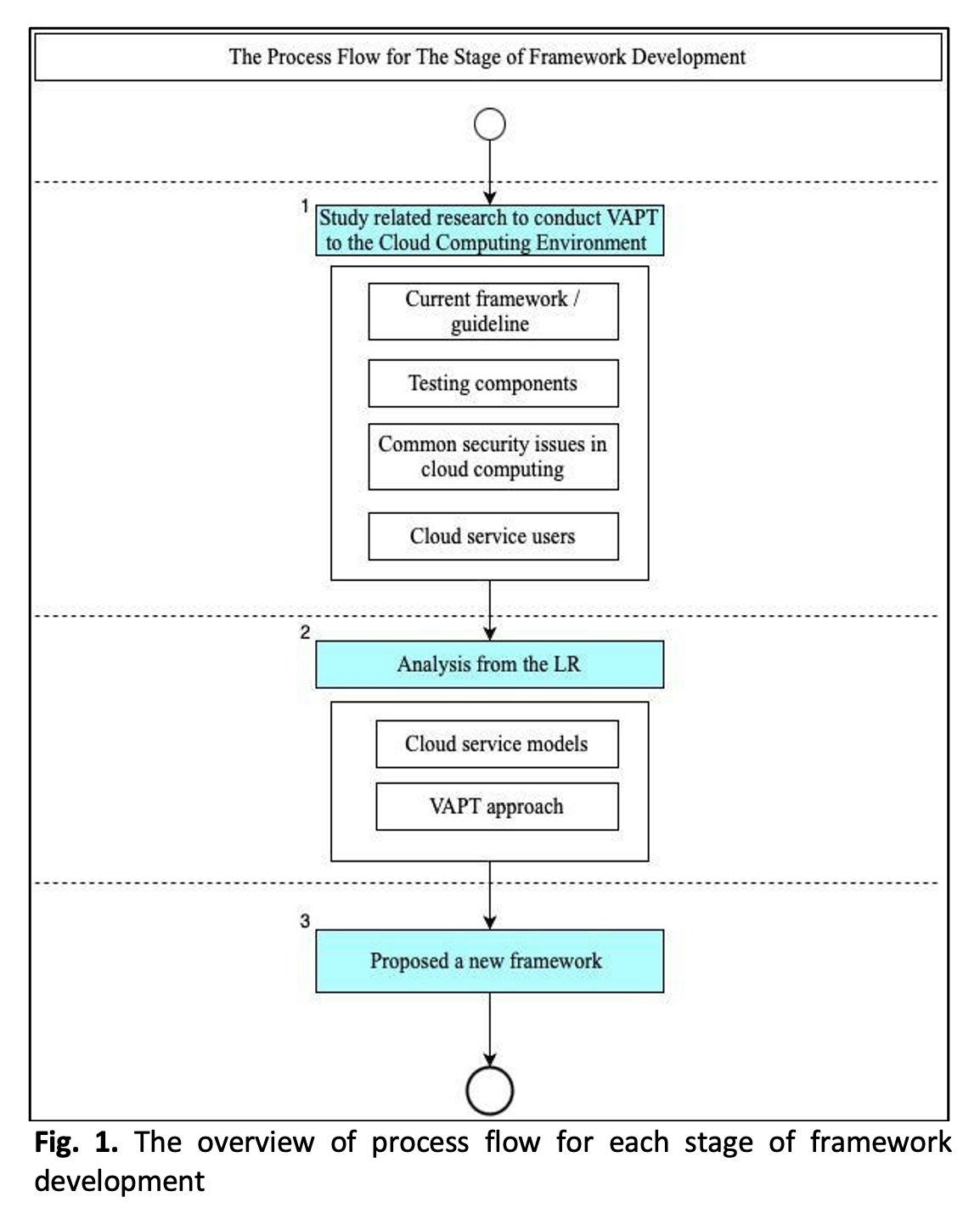
Penetration testing is a process that focuses on finding security vulnerabilities in a target environment that could let an attacker penetrate the network or computer system or steal information. Due to the COVID-19 endemic, most employees still implement working from home or a hybrid approach, even though the number of new cases of COVID-19 is decreasing. However, working from home depends mainly on cloud computing applications that help employees efficiently accomplish their daily work. This situation also increased the number of data generated from various sources, so they may be exposed to different security risks. This research will propose a framework to conduct vulnerability assessment and penetration testing (VAPT) in cloud service models such as SaaS, PaaS, and IaaS from the perspective of penetration testers. This proposed framework is developed through the integration and mapping of existing frameworks and guidelines to conduct VAPT on testing components such as web applications, APIs, network testing, etc. In this proposed framework, the method of conducting VAPT for each cloud service model will be discussed in detail, from the planning and reconnaissance stage until the report is delivered to the cloud subscriber or cloud provider. An advantage of this proposed framework for the penetration tester is that there is still a lack of methods or guidelines for conducting VAPT that cover all the cloud service models in one comprehensive document
Downloads