A Novel Approach for Block Chain Technology based Cyber Security in Cloud Storage Using Hash Function
DOI:
https://doi.org/10.37934/araset.32.3.178189Keywords:
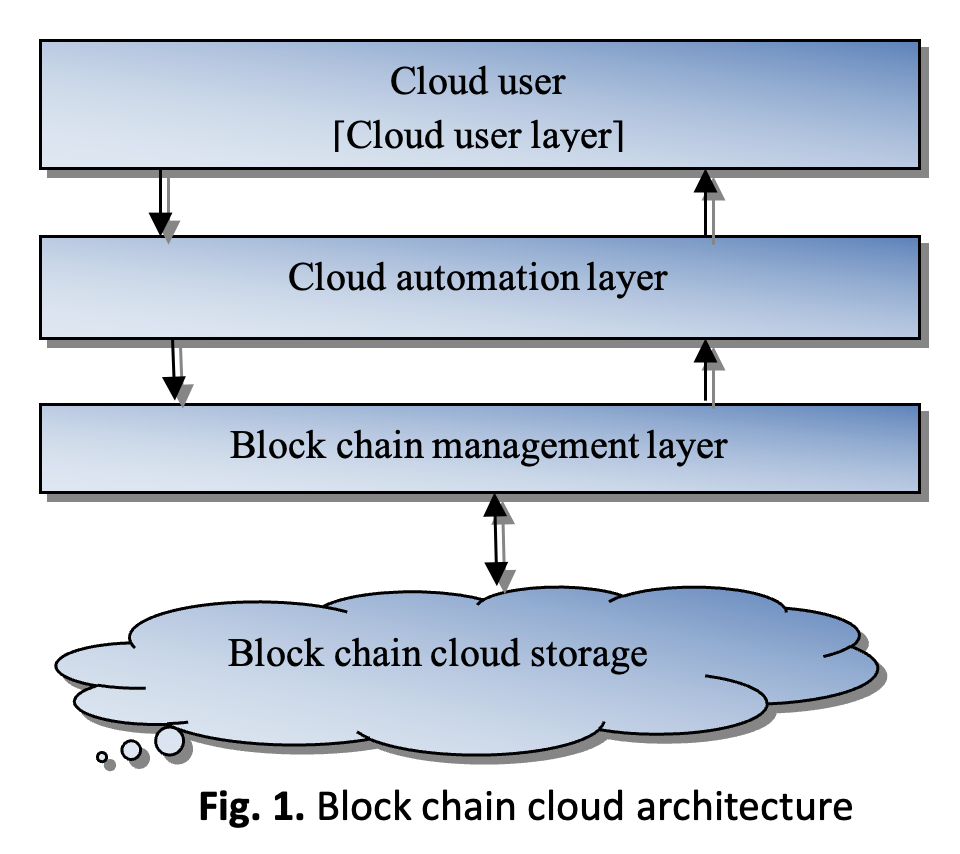
Block chain management layer, Distributed computing, Block chain cloud storage, blockchain-based Secure InformationAbstract
Block chain is generic name to describe the technology used by Bitcoin and other digital currency to record and secure transaction. This technology enables a highly accessible ledger with greatly reduced risk for tampering. The dynamic immutable, data ledger makes ideal for real time monitoring of the shipment of goods. Cloud is an important of distributed storage system of networking. Cloud system need for security, storage management, minimize the cloud cost and fast storage could be improved. The security using new most development security system of block chain technology is used to improve the cloud security. The data owner to be uploads the data on web page and access the folder. The user has been accessing the data on cloud storage using encryption and decryption using block chain based cyber security system. the problem for security in cloud storage because data transmission and data sharing, the alternate for security solution using Post Quantum-proof cryptography algorithm is used to improve the encryption and decryption process and more tight security for block chain technology for the cloud system. The SHA-3 512 Hash function algorithm automatically generate the key for data security enhancements of cloud networks. Post Quantum-proof cryptography algorithm has been improved the encryption Performance and reduced the power consumption, and increase the Latency performance, and boost up the security performances. Finally Post Quantum-proof cryptography algorithm for well support for security system of the cloud networks. Even some passwords, which are often cited as the weakest link in cyber security, may not be necessary.Downloads
Download data is not yet available.
Downloads
Published
2023-10-05
Issue
Section
Articles



























