Privacy Preserving Image Retrieval Using Multi-Key Random Projection Encryption and Machine Learning Decryption
DOI:
https://doi.org/10.37934/araset.42.2.155174Keywords:
Privacy Preservation, Random Projection, Machine LearningAbstract
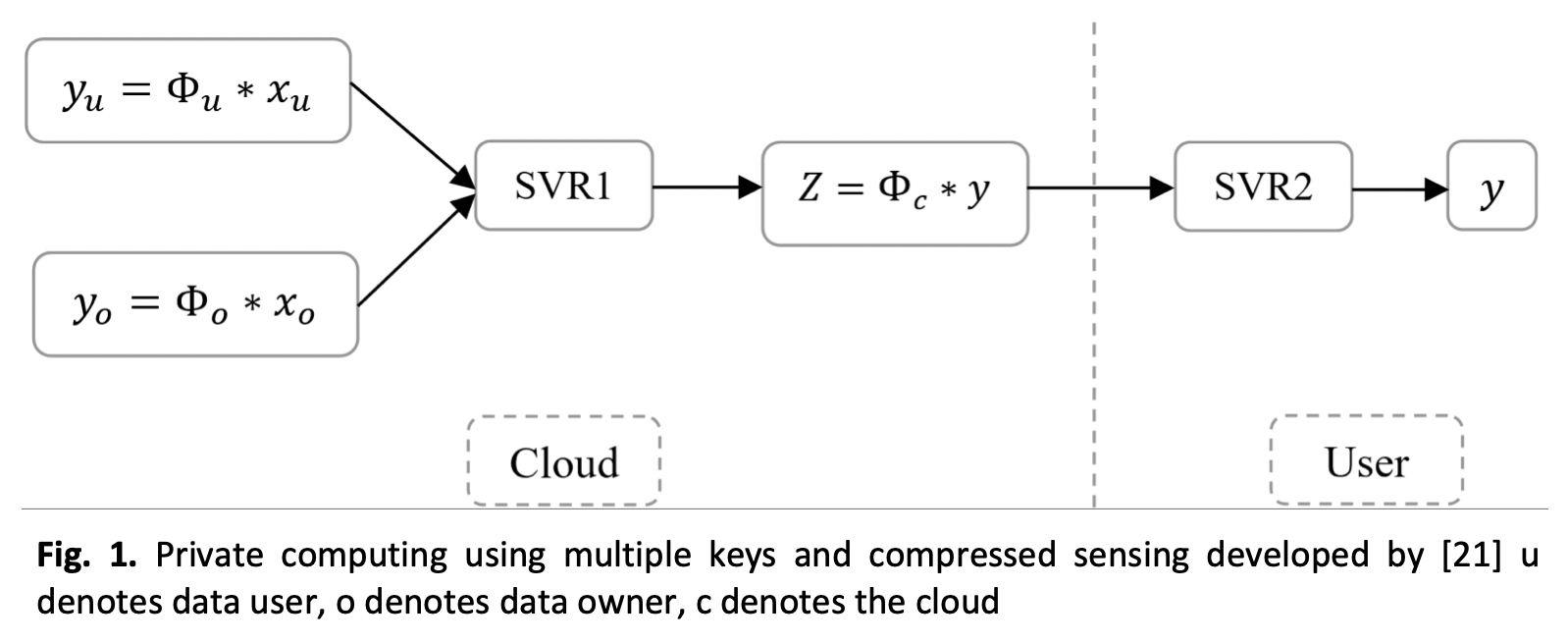
Homomorphic Encryption (HE), Multiparty Computation (MPC), Differential Privacy (DP) and Random Projection (RP) have been used in privacy preserving computing. The main benefit of the random projection approach is the lighter time and space complexity compared to the other available techniques. However, RP is typically used in a symmetric encryption mode, with one random projection matrix single key, making it vulnerable to attacks. An enhanced multi-key RP approach is proposed in this paper where a set of N random matrices are used as projection keys. Moreover, a randomly chosen one is used for each new query. Machine learning models are trained to perform specific vector operations on the randomly projected vectors and produce another randomly projected results vector. Another machine learning model is trained to decrypt the final result at the user’s side. The proposed system is shown to offer privacy against known plaintext and cipher-only attacks while preserving Euclidean distance calculations accuracy in the randomly projected domain which are demonstrated on the COREL 1K image retrieval task. Results show that the cyphertext space took sixteen times less than the ciphertext done with homomorphic encryption, and the computation of distance using random projection was 8 times faster than homomorphic encryption distance calculation.
Downloads