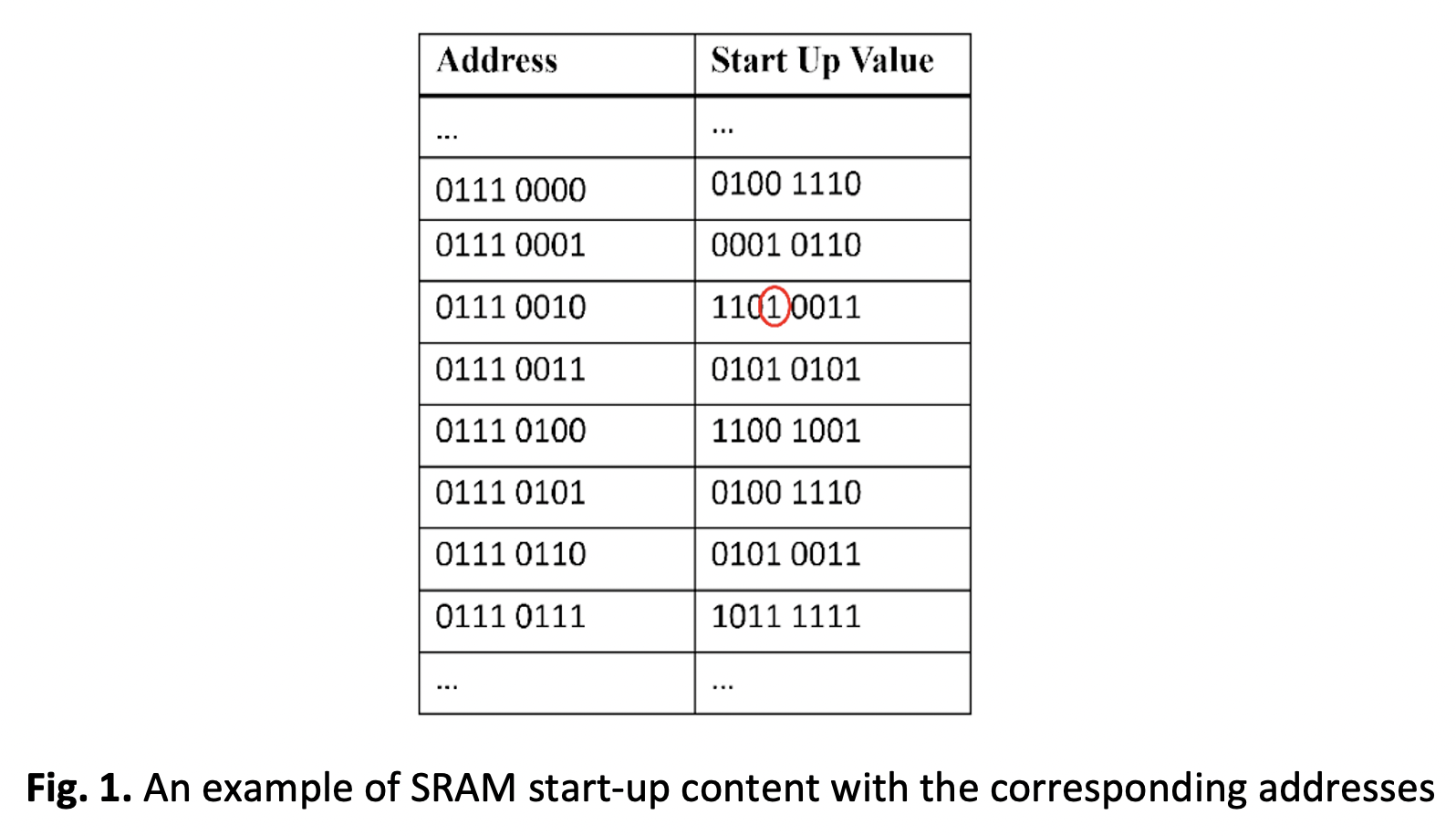
Data Remanence Based Approach towards Stable Key Generation from Physically Unclonable Function Response of Embedded SRAMs using Binary Search
DOI:
https://doi.org/10.37934/araset.35.2.114131Keywords:
Physically unclonable function, binary search, data remanence, authenticationAbstract
Today’s device authentications in IoT devices use public and private key cryptography. Nevertheless, they are still vulnerable to threats because keys or device IDs digitally stored in IoT devices can be stolen or cloned. In contrast, SRAM PUFs utilize physical variations in memory cells of embedded SRAM in microcontrollers or standalone SRAM chips. These inherent physical characteristics are unpredictable and practically impossible to duplicate. They are negligible to affect regular SRAM operation but large enough to be used for authentication purposes in SRAM PUFs operation. However, SRAM PUFs have poor stability and a relatively high bit error rate (BER). Temporal Majority Voting (TMV) and other error correction codes (ECCs) have improved SRAM PUFs performance, but they require a lot of processing time and hardware resources. The data remanence nature of SRAM cells can be utilized to select SRAM PUFs bits with much lower BER and more stable bits, but a suitable algorithm is required to find the best possible power-off time for each type of chip. This paper proposes using the data remanence method and binary search algorithm to obtain the strong SRAM PUFs characteristics of the selected SRAMs at the optimal power-off time. These SRAMs include embedded SRAMs of AtMega328P, STM32F108C, ESP8266 microcontrollers, and an off-the-shelf SRAM chip 23LC1024-I/P, which are being used in various IoT applications. The strong SRAM PUF has more stable characteristics that reduce BER to 0% and increase stability to 99.999%. This proposed method can be utilized on any IoT platform which deals with essential data and requires less resource-hungry security and authentication protocols.Downloads
Download data is not yet available.