An Enhanced Dual-Layer Video Steganographic Approach: Enhancing Security and Imperceptibility
DOI:
https://doi.org/10.37934/araset.58.1.119Keywords:
Data hiding, video steganography, least significant bit (LSB), pixel selection technique, dual layered techniqueAbstract
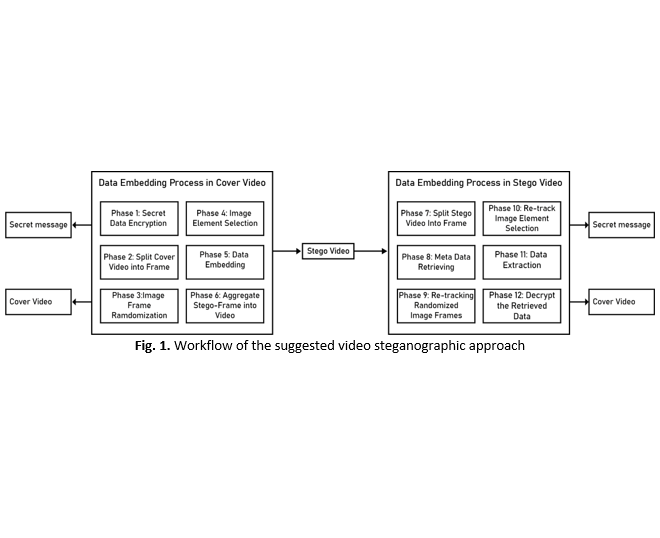
In a digital age where the role of digital information is continually expanding, the imperative to ensure secure communication and data protection has intensified. Steganography, a field that conceals sensitive information within apparently innocuous carriers like multimedia files, holds promise for achieving this goal. Recent times have seen a growing interest in video-based steganography, driven by the proliferation of videos online. However, a review has unveiled a noteworthy gap in efforts to increase the safety of video steganography employing the popular Least Significant Bit (LSB) process. LSB steganography is at risk to exploits that could jeopardize the confidentiality of the concealed message. In this research, we present a video steganographic solution achieved through the integration of advanced encryption algorithms and a dual approach involving randomized frame selection using the Fisher-Yates method and pixel selection utilizing the 8-directional technique. Additionally, we have devised an upgraded imperceptible video steganographic approach in the spatial domain, capitalizing on an XOR-based LSB substitution embedding approach. The outcomes underscore the effectiveness of our proposed methodology, revealing significant imperceptibility when compared to recent solutions, thereby reinforcing data security against unauthorized access. This comprehensive solution holds wide-ranging applications across various domains, providing heightened security and confidentiality for sensitive information. Notable applications include secure communications within intelligence agencies, safeguarding patient data in medical sciences, ensuring privacy in video surveillance, fortifying video transmission against errors and data breaches, securing business communications, preventing data leakage, and enhancing rights management for digital content.